

A simple centralized approach for solving actual licensing and service protection problems in SDIs using FOSS
Eurogeographics - INSPIRE KEN Service/Data Webinar 26.11.2013

NUTS 3 Level: 36
LAU 1 Level (Collective municipalities): 198
LAU 2 Level (Municipalities): 2459
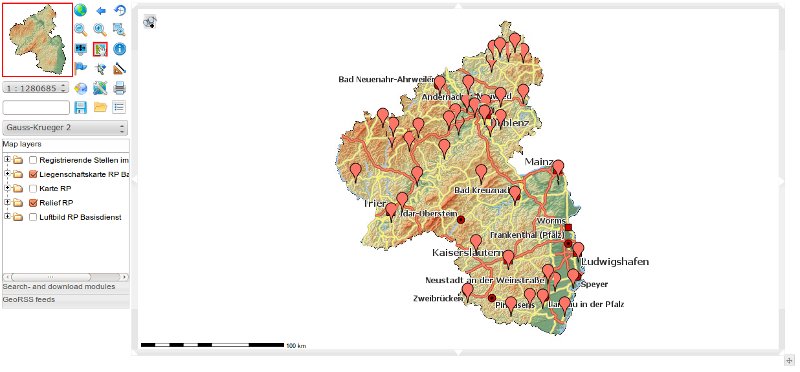
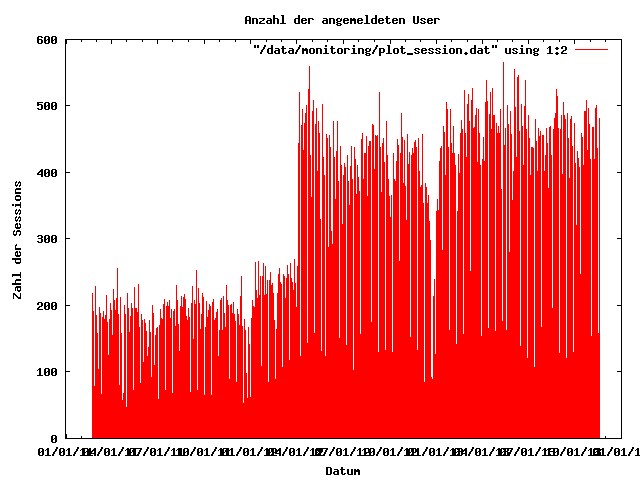
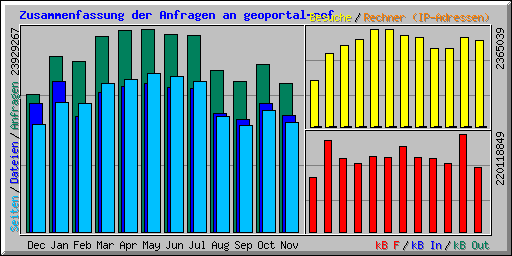
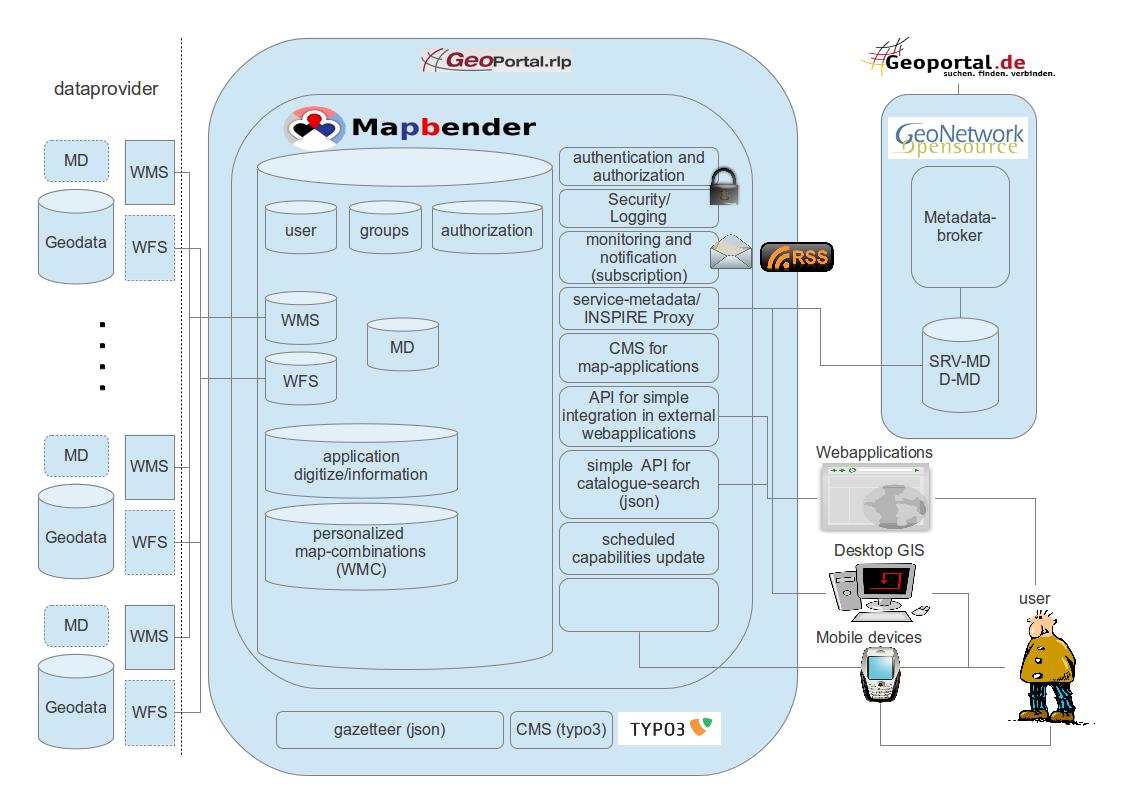
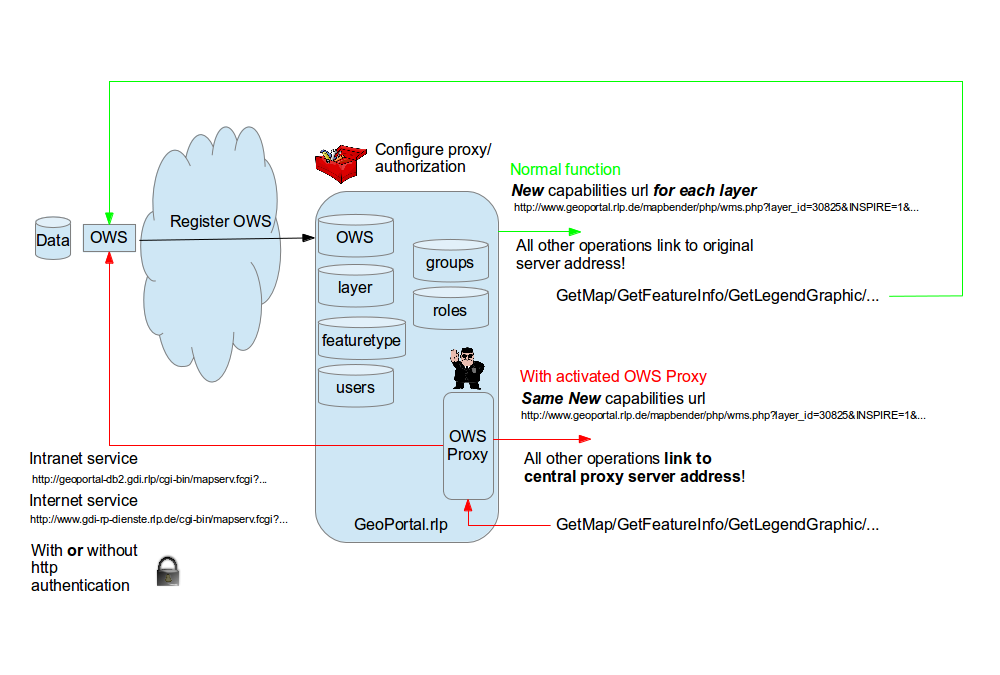
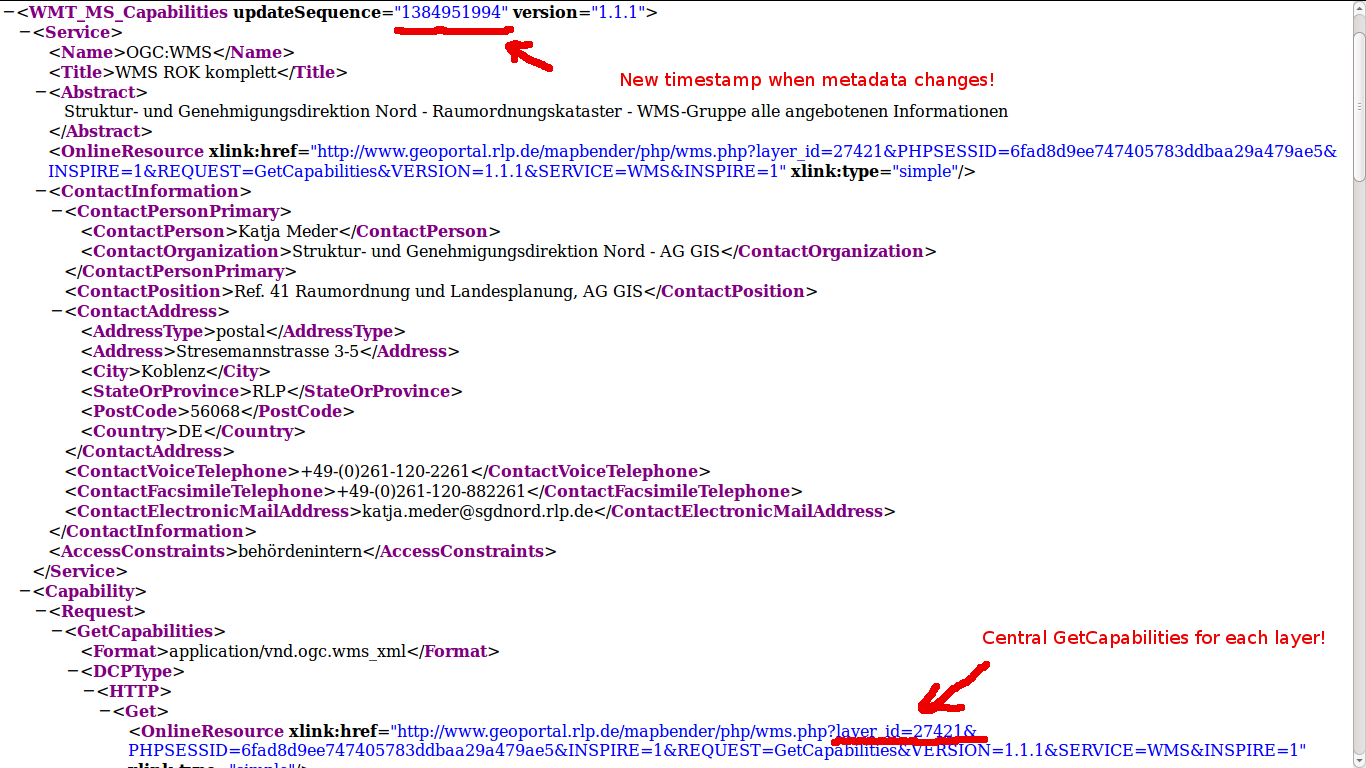
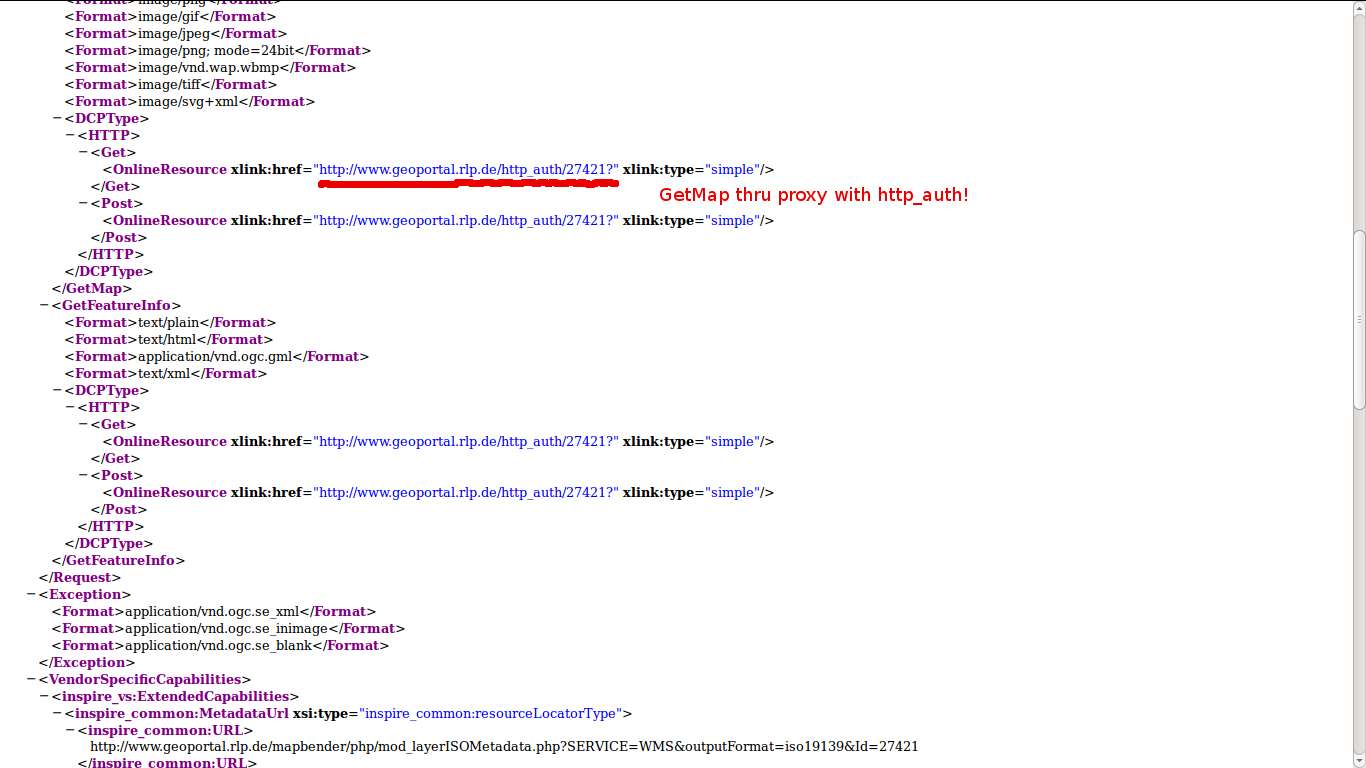
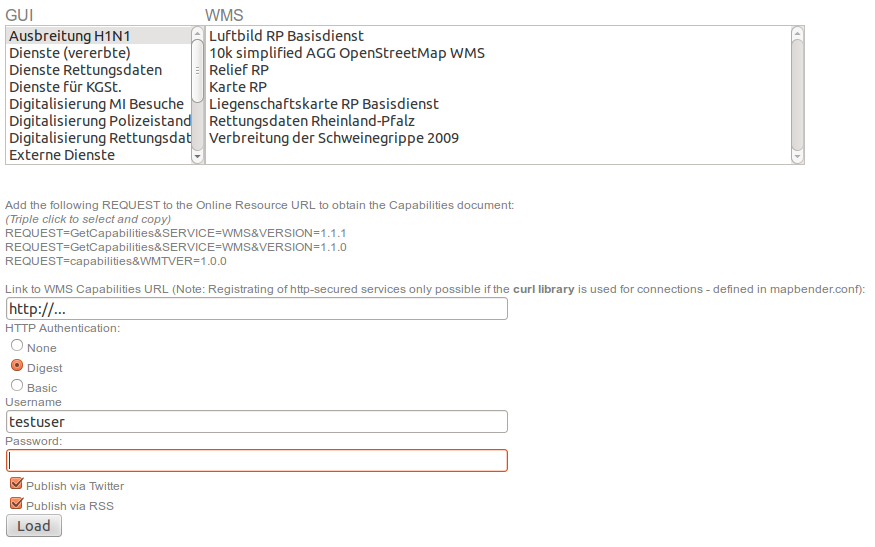
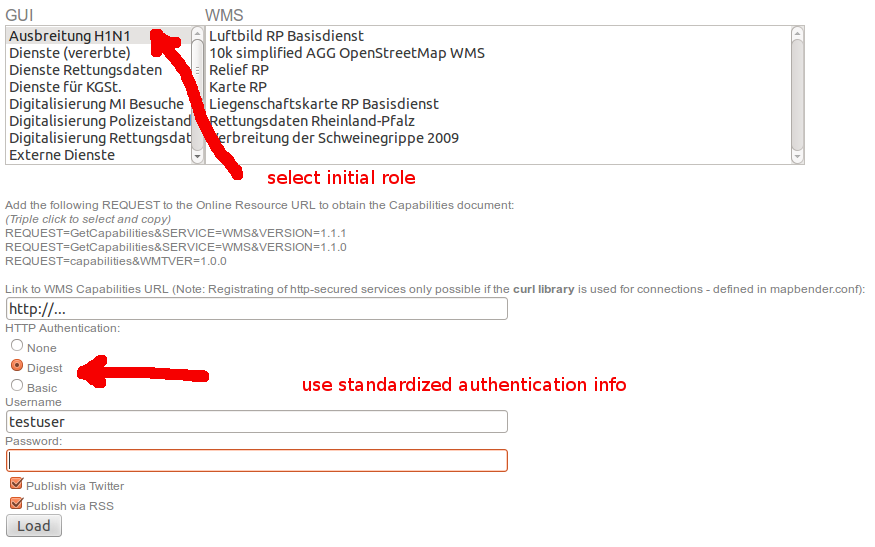
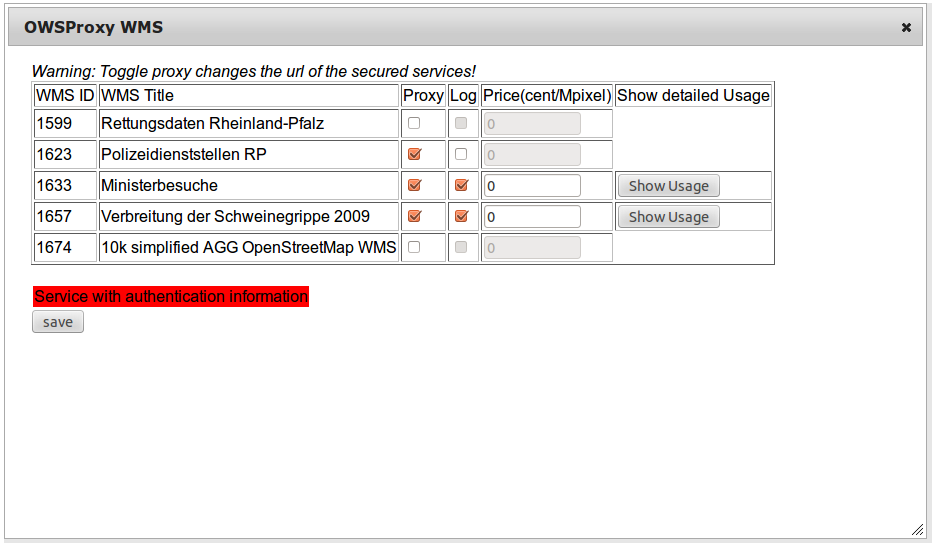
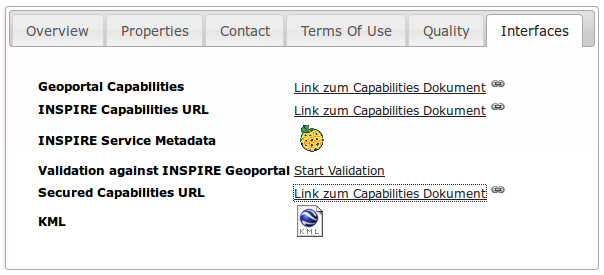
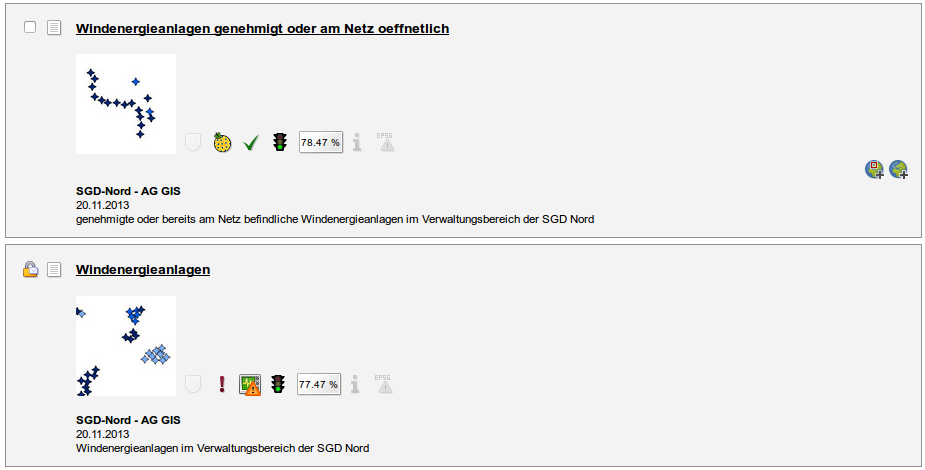
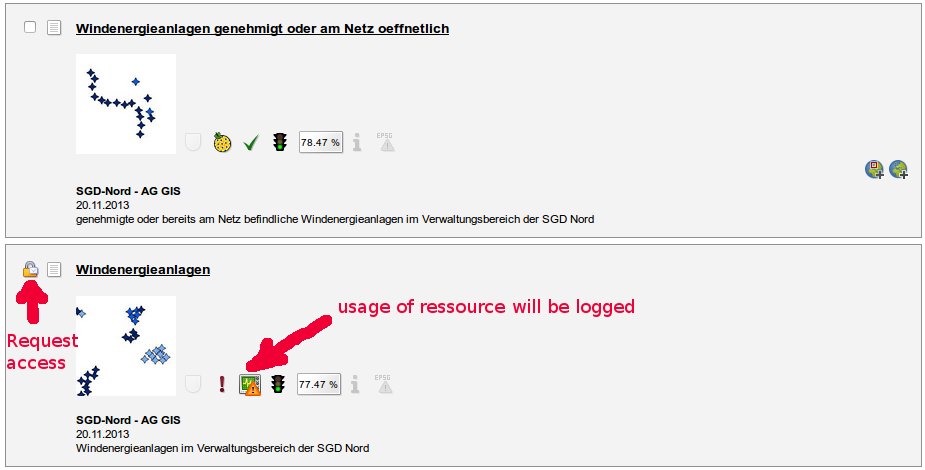
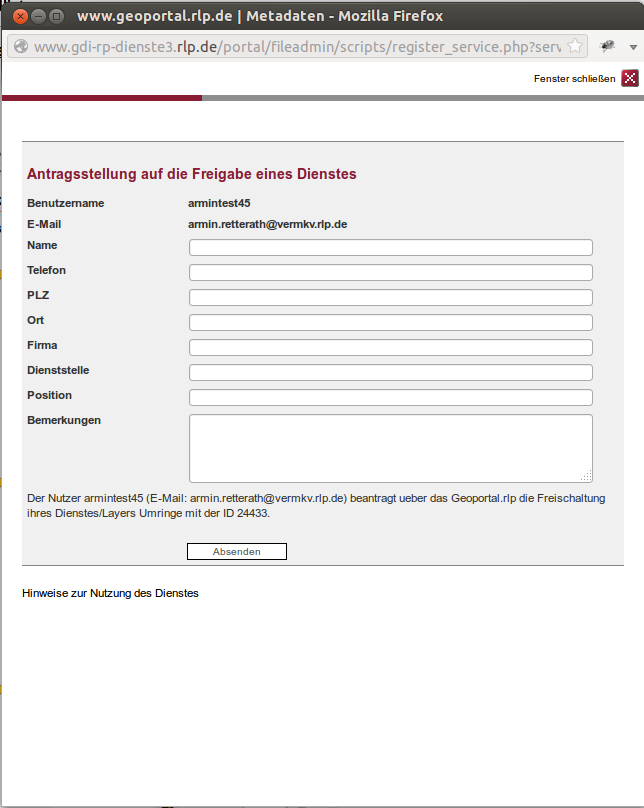
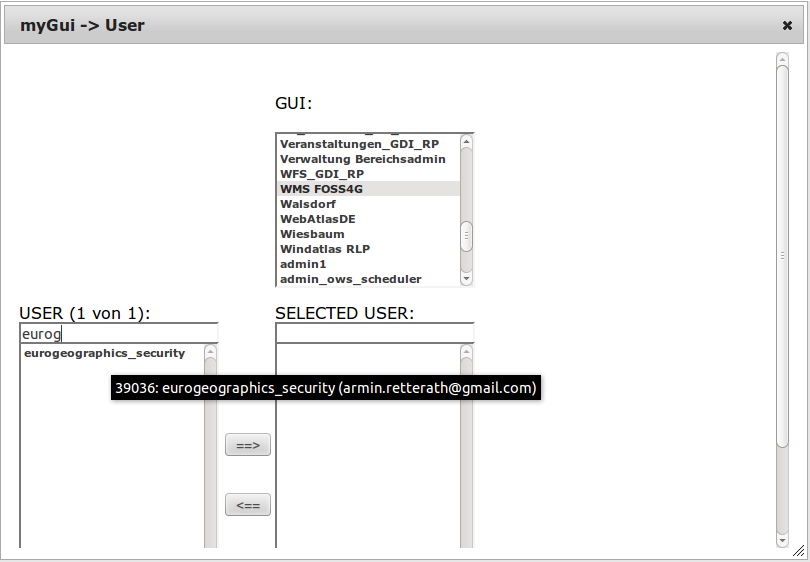
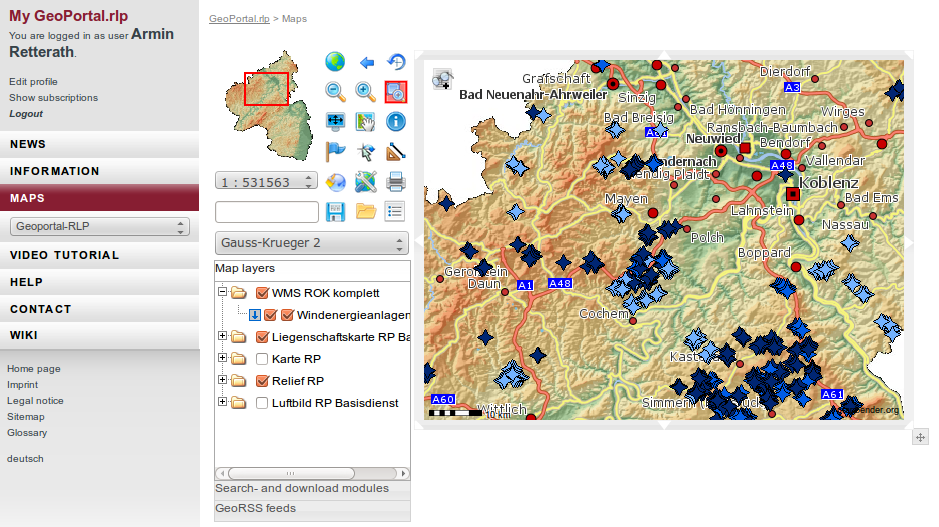
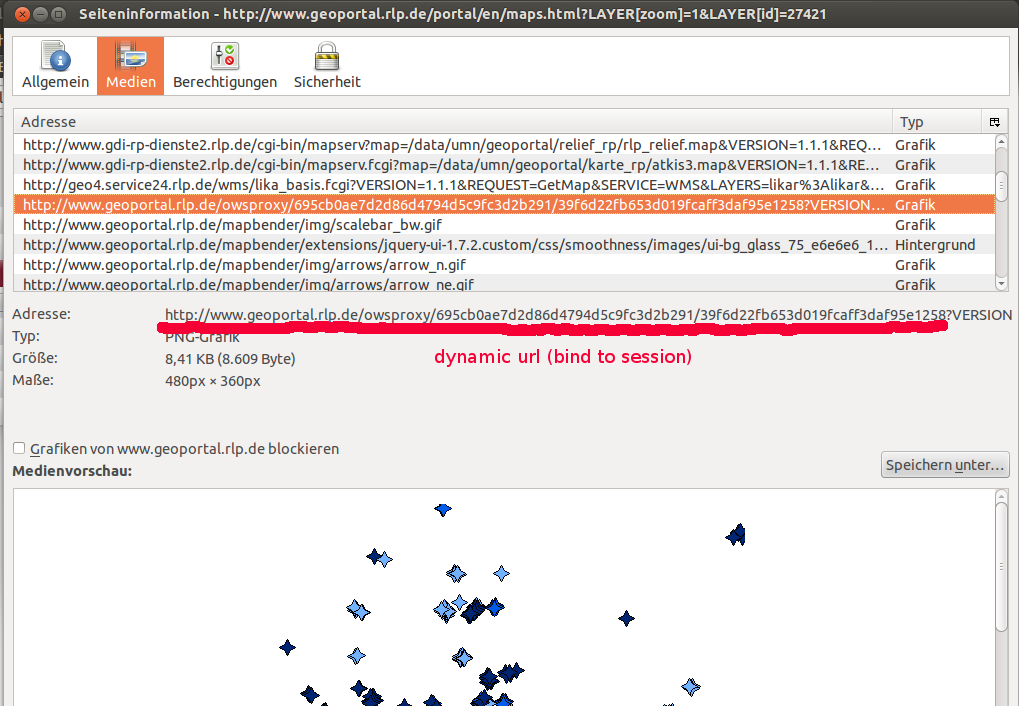
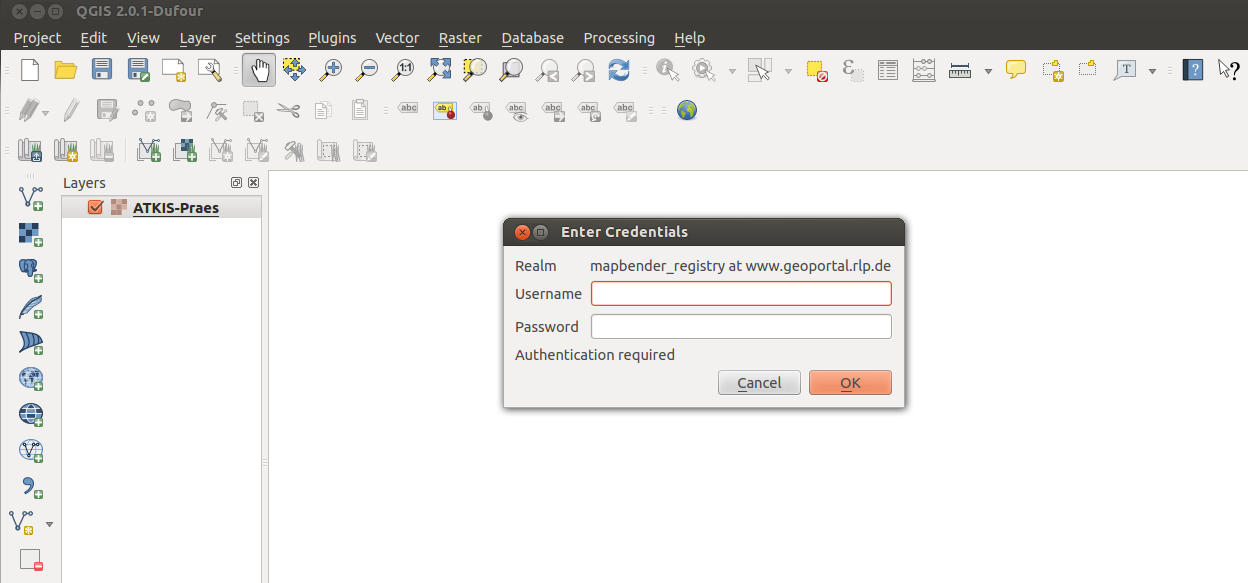
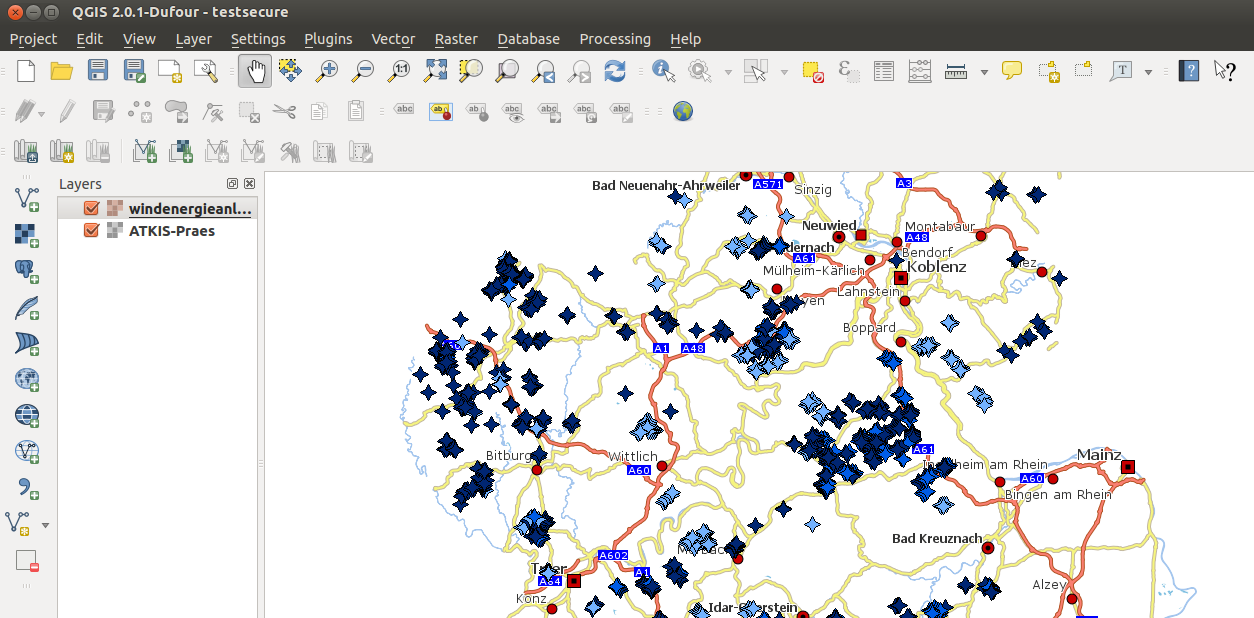
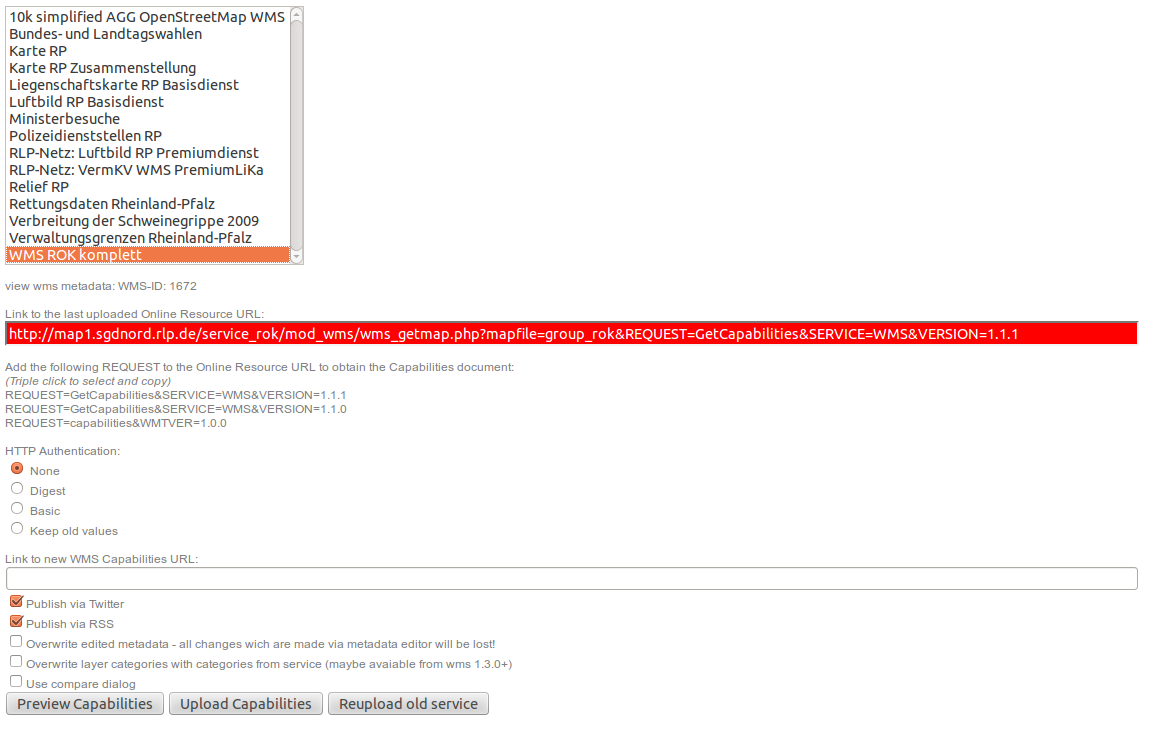
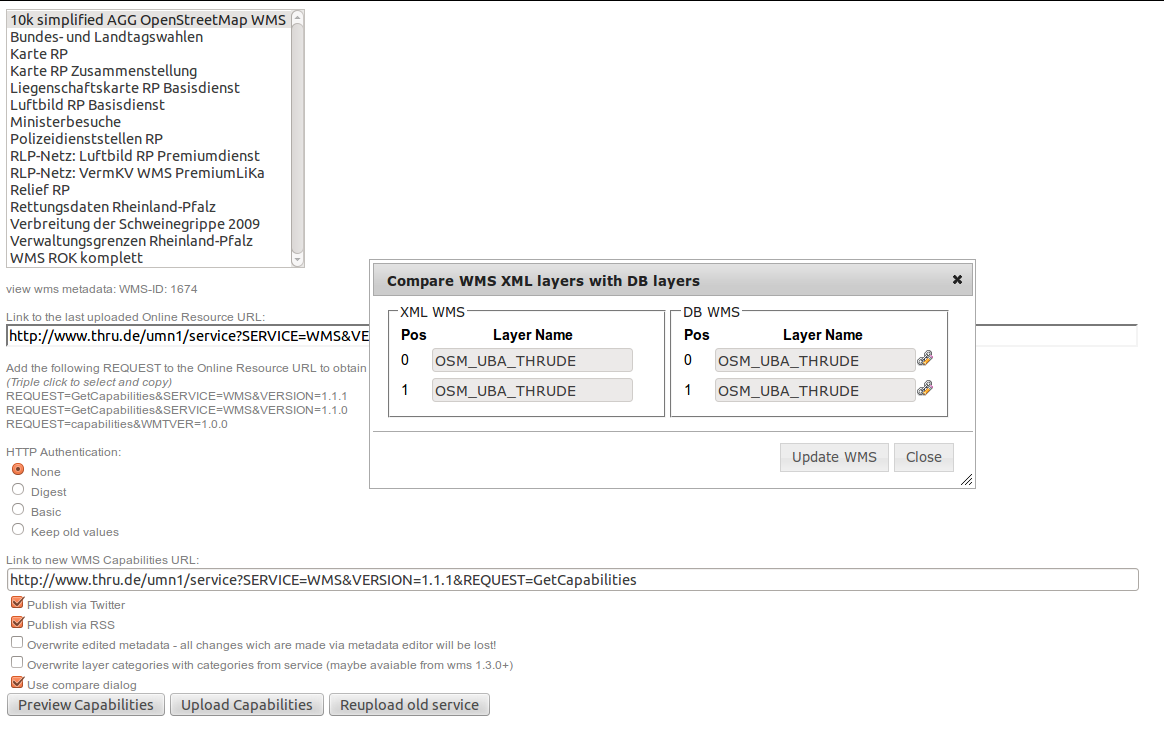
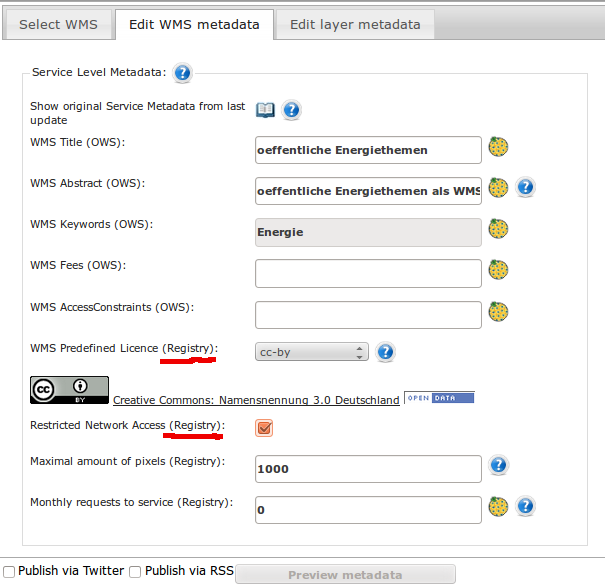
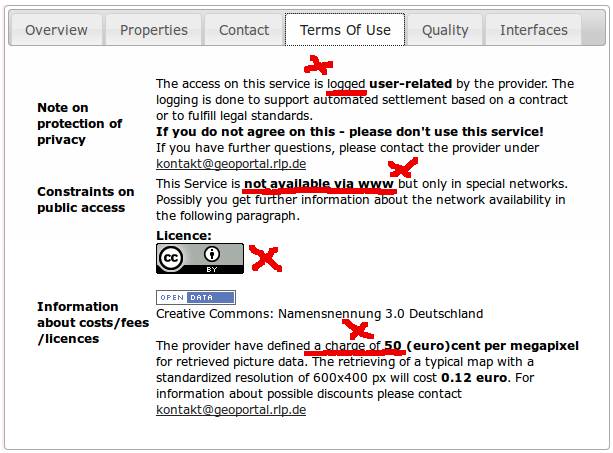
... and can be downloaded as VM for testing